Navigating the intricate realm of network management can be daunting, especially when it comes to securely accessing and configuring your MikroTik routers. Winbox login emerges as a powerful tool, providing network administrators with a user-friendly yet robust interface to manage their devices efficiently. By mastering the process of Winbox login, users can harness the full potential of MikroTik’s advanced features, optimize network performance, and enhance security protocols. This comprehensive guide aims to illuminate every facet of the Winbox login process, ensuring you have the confidence and knowledge to manage your network devices with ease.
Understanding the Significance of Winbox Login in Network Management
Establishing a Winbox login session is the gateway to configuring and controlling your MikroTik routers. It’s more than just entering credentials—it’s about understanding how this access point integrates into your overall network security and management strategies.
Before diving into the step-by-step procedures, it’s critical to recognize why Winbox login is essential. MikroTik’s Winbox utility provides a graphical user interface (GUI) that simplifies interaction with router configurations, especially for those who find command-line interfaces intimidating or cumbersome. This utility is designed specifically for Windows environments but can be run on other operating systems using compatibility tools.
A successful Winbox login ensures that you can configure network parameters, monitor traffic, set up security rules, and troubleshoot issues efficiently. Furthermore, secure login practices prevent unauthorized access, safeguarding your network’s integrity. Whether managing a small office network or a large ISP infrastructure, understanding the importance of proper Winbox login procedures forms the backbone of effective network administration.
The Role of Winbox Login in Securing Network Devices
Security is paramount in modern networks, and the first line of defense begins with proper authentication. Winbox login facilitates this by requiring a username and password, or other authentication methods, ensuring only authorized personnel can access sensitive configuration settings.
The process also involves understanding how to establish a secure connection—such as using MAC address access or IP-based login—and the importance of implementing additional security layers like VPNs or SSH tunneling for remote access. These measures protect the login session from interception or unauthorized access, especially over public or unsecured networks.
Moreover, regular updates to firmware and changing default credentials post-initial setup are vital. By mastering the Winbox login process, network administrators can also set up and enforce policies like two-factor authentication (2FA), further strengthening the network’s security posture.
Default Settings and Initial Configuration for Winbox Access
Newly purchased MikroTik routers often come with default usernames and passwords, making understanding initial setup crucial. These defaults often include a username “admin” with an empty password or a preset password, which poses security risks if not changed promptly.
It’s recommended to perform an initial configuration using Winbox before deploying the device in a live environment. This involves physically connecting the device to your computer via Ethernet, finding the device on your network, and establishing a login session. During these initial steps, it’s necessary to assign a new password, configure basic network parameters, and disable or modify default settings that could be exploited.
Understanding the default access methods and best practices for secure initial configurations ensures that your network remains protected from threats right from the outset. This proactive approach helps prevent unauthorized access and sets the stage for a resilient network infrastructure.
How to Access Your MikroTik Router via Winbox Login: Step-by-Step Guide
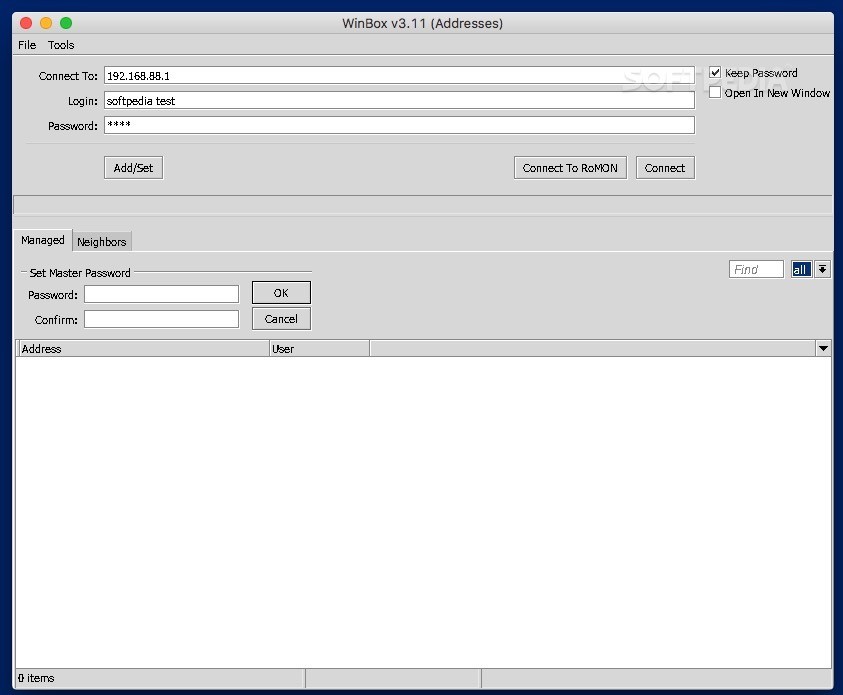
Getting started with Winbox login may seem straightforward, yet many users encounter issues due to network configurations or missteps. This section offers a clear, detailed step-by-step guide to successfully access your MikroTik device.
Before proceeding, ensure your computer is connected directly to the router via Ethernet cable or is on the same network segment. Open the Winbox utility—downloadable from MikroTik’s official website—and prepare your device’s login credentials or MAC address.
Understanding each step thoroughly can save troubleshooting time and prevent common errors such as IP conflicts or firewall restrictions. The process involves locating your router, establishing a connection, and verifying access parameters, all crucial for smooth management.
Preparing Your Network for Winbox Connection
Preparation is key to ensuring a successful Winbox login. Begin by verifying your computer’s network settings—set your IP address within the same subnet as the router, or use DHCP if enabled on the router. Disable any VPNs or firewalls that may interfere with local network traffic, and ensure the router is powered on and properly connected.
Next, confirm the device’s IP address. You can do this by checking your network’s DHCP client list or using network discovery tools like Advanced IP Scanner. Having the correct IP address or MAC address of the MikroTik device is essential for finding it within Winbox.
Creating a stable initial connection prevents frustration later and allows you to focus on configuration. Remember, if your router’s IP address isn’t known, Winbox offers a neighbor discovery feature to scan the local network automatically.
Establishing the Winbox Login Session
Once your network is prepared, launch the Winbox utility. You will encounter the connection window, which displays options for “Connect To,” “Login,” and “Password.” In the “Connect To” field, input the router’s IP address or select it from the MAC address list if IP access is restricted.
If using the IP address, select the correct interface—Ethernet or Wi-Fi. Enter your username and password—default is usually “admin” with no password, but this should be changed immediately after first login. Click “Connect” to establish the session.
Upon successful login, a graphical interface opens, allowing you to navigate the device’s configuration settings. If the connection fails, check for IP conflicts or firewall blocks, and ensure your credentials are correct. You may also try disabling security software temporarily to identify possible interference.
Troubleshooting Common Winbox Login Problems
Encountering problems during Winbox login can be frustrating, but most issues are resolvable with systematic troubleshooting. Common causes include incorrect IP addresses, firewall restrictions, password errors, or physical connectivity issues.
Ensure that your computer’s network settings are properly configured to communicate within the router’s subnet. Check the physical connections and confirm the router is powered on. If you experience repeated login failures, verify that the user account has not been disabled or modified to restrict access.
Utilize logs and message alerts for diagnostic clues. MikroTik routers provide logs accessible through Winbox or via CLI, revealing failed login attempts or security alerts. Adjust your firewall settings to permit Winbox traffic (default TCP port 8291), and ensure your system date/time is correct—which can influence authentication tokens.
In cases where connection issues persist, resetting the router to factory defaults and reconfiguring might be necessary. Always document your credentials and settings before performing such resets.
Best Practices for Maintaining Secure and Efficient Winbox Login Access
Maintaining secure and efficient Winbox login practices is vital for ongoing network health and security. Best practices involve setting strong credentials, employing access controls, and establishing procedures for routine management.
A key aspect is changing default passwords immediately after initial setup, using complex and unique passwords for each device. Avoid using common passwords or easy-to-guess combinations to prevent brute-force attacks.
Implement access restrictions by binding Winbox access to specific IP addresses or network segments. This minimizes exposure and prevents unauthorized login attempts from outside your trusted network environment. Using SSH tunneling or VPNs adds additional security layers, encrypting the connection for remote management.
Routine updates to MikroTik firmware and regular audits of user access rights keep the network fortified against emerging threats. Documenting login attempts and maintaining logs can also help identify suspicious activity early, enabling prompt mitigation measures.
Establishing automation where possible, such as remote scripts for configuration backups or scheduled maintenance, can streamline management and reduce human error. Training staff and creating clear access policies foster a security-aware culture, ensuring Winbox login procedures are consistently followed and vulnerabilities minimized.
Conclusion
Mastering the Winbox login process is an essential skill for anyone involved in managing MikroTik network devices, blending security, efficiency, and control. By understanding the importance of login procedures, preparing networks properly, troubleshooting effectively, and adhering to best practices, network administrators can unlock the full potential of their devices while safeguarding their infrastructure. As networks evolve, so too should our strategies for secure and seamless access—making Winbox login not just a routine task but a cornerstone of robust network management.


